How to restrict WhatsApp permissions
What used to be the SMS is done today via messenger over the mobile Internet.
And the success of messenger services was ultimately a logical consequence, since not every message costs a few cents, which lapp themselves quickly over time to a few euros!
The data volumes to be transmitted are also kept within limits (at least as long as primarily text is being sent), so that the volume of data is only used insignificantly. Now it is so that unfortunately there is nothing really free in life. The price you pay for WhatsApp, for example, is significantly more valuable to the company than the quick money.

It’s about your data!
And not just those that you specified during the installation, but all data (such as photos, contacts, appointments and documents) that are on your smartphone.
At the latest since the acquisition of WhatsApp by Facebook, the path of precisely this data is no longer comprehensible to the user.
Of course, there are also alternatives to WhatsApp, but since they do not have this high prevalence, they are unfortunately hardly used, although they offer an end to end encryption, without compromising the comfort appreciably.
You can find out how to control and restrict the rights of WhatsApp and other apps on your smartphone in our article.
How to restrict WhatsApp permissions
What used to be the SMS is done today via messenger over the mobile Internet.
And the success of messenger services was ultimately a logical consequence, since not every message costs a few cents, which lapp themselves quickly over time to a few euros!
The data volumes to be transmitted are also kept within limits (at least as long as primarily text is being sent), so that the volume of data is only used insignificantly. Now it is so that unfortunately there is nothing really free in life. The price you pay for WhatsApp, for example, is significantly more valuable to the company than the quick money.

It’s about your data!
And not just those that you specified during the installation, but all data (such as photos, contacts, appointments and documents) that are on your smartphone.
At the latest since the acquisition of WhatsApp by Facebook, the path of precisely this data is no longer comprehensible to the user.
Of course, there are also alternatives to WhatsApp, but since they do not have this high prevalence, they are unfortunately hardly used, although they offer an end to end encryption, without compromising the comfort appreciably.
You can find out how to control and restrict the rights of WhatsApp and other apps on your smartphone in our article.
1. Check WhatsApp permissions.
1. Check WhatsApp permissions.
As of Android version 6.0, you can now finally control the permissions of apps with on-board resources, and not only see them once during the installation.
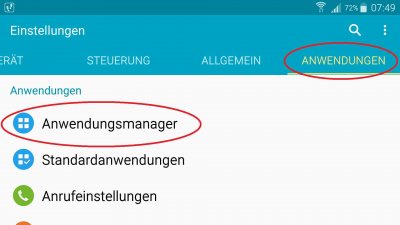
To view and control the permissions of applications, first call the application manager:
“Settings” – “Applications” – “Application Manager“.
There you will find all installed apps that you can now select separately. In the submenu of the respective app, the most important data (such as energy consumption, data usage, etc.) is displayed.
Here you select the item “Permissions”, and you can activate or deactivate these.
See picture: (click to enlarge)
Of course, you have the option to turn on or off all permissions as you like, but you may have to reckon with a reduced range of functions right through to inability to function.
Here we simply recommend to check the permissions according to the exclusion principle, and then simply undo the steps.
As of Android version 6.0, you can now finally control the permissions of apps with on-board resources, and not only see them once during the installation.
To view and control the permissions of applications, first call the application manager:
“Settings” – “Applications” – “Application Manager“.
There you will find all installed apps that you can now select separately. In the submenu of the respective app, the most important data (such as energy consumption, data usage, etc.) is displayed.
Here you select the item “Permissions”, and you can activate or deactivate these.
See picture:
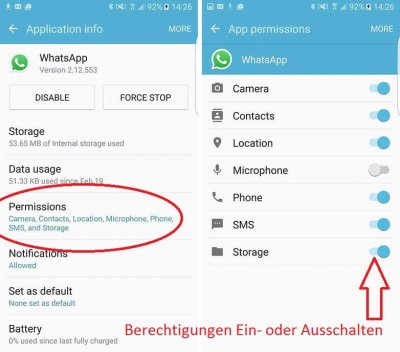
Of course, you have the option to turn on or off all permissions as you like, but you may have to reckon with a reduced range of functions right through to inability to function.
Here we simply recommend to check the permissions according to the exclusion principle, and then simply undo the steps.
2. Alternatives to WhatsApp.
2. Alternatives to WhatsApp.
WhatsApp is of course a very good messenger, and not least because of its accessibility market leader in this field.
However, he also has to be criticized for the difficulty of reproducing and controllable handling of users’ personal data.
There are alternatives that make it better:
Threema:
Represents a safe alternative to WhatsApp and is aimed primarily at users attach importance to the protection of your personal information.
After the initial installation, set a key pair for decoding and decoding the Incoming and outgoing messages, and register once by e-mail address or phone number. For a detailed description of the range of functions and the encryption technologies, see the manufacturer’s FAQ: Click here
Here you can download the Threema Messenger for Android: Threema Download
Telegram:
Basically a WhatsApp clone with almost identical functionality. Visually, the messenger reminds strongly of the top dog. Your contacts are also conveniently taken from the address book here.
When it comes to security, telegrams can score with a 256-bit encryption, but they clearly lag behind Threema in terms of data protection.
A detailed FAQ can be found on the manufacturer page: Click here
Here you can download the Telegram Messenger for Android: Telegram Download
WhatsApp is of course a very good messenger, and not least because of its accessibility market leader in this field.
However, he also has to be criticized for the difficulty of reproducing and controllable handling of users’ personal data.
There are alternatives that make it better:
Threema:
Represents a safe alternative to WhatsApp and is aimed primarily at users attach importance to the protection of your personal information.
After the initial installation, set a key pair for decoding and decoding the Incoming and outgoing messages, and register once by e-mail address or phone number. For a detailed description of the range of functions and the encryption technologies, see the manufacturer’s FAQ: Click here
Here you can download the Threema Messenger for Android: Threema Download
Telegram:
Basically a WhatsApp clone with almost identical functionality. Visually, the messenger reminds strongly of the top dog. Your contacts are also conveniently taken from the address book here.
When it comes to security, telegrams can score with a 256-bit encryption, but they clearly lag behind Threema in terms of data protection.
A detailed FAQ can be found on the manufacturer page: Click here
Here you can download the Telegram Messenger for Android: Telegram Download
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.

































