Smartphone Wi-Fi security: Public hotspots vs. home network
The smartphone has become the central hub of our digital lives. We use it for confidential banking transactions, private communication, and accessing company data. Wireless connectivity via Wi-Fi is by far the most convenient, but often also the most vulnerable interface. While we usually feel safe at home, public hotspots often resemble a digital minefield.
In this article, we analyze the technical threats in detail, explain the evolution of encryption standards, and provide a well-founded assessment of smartphone use within the home network.
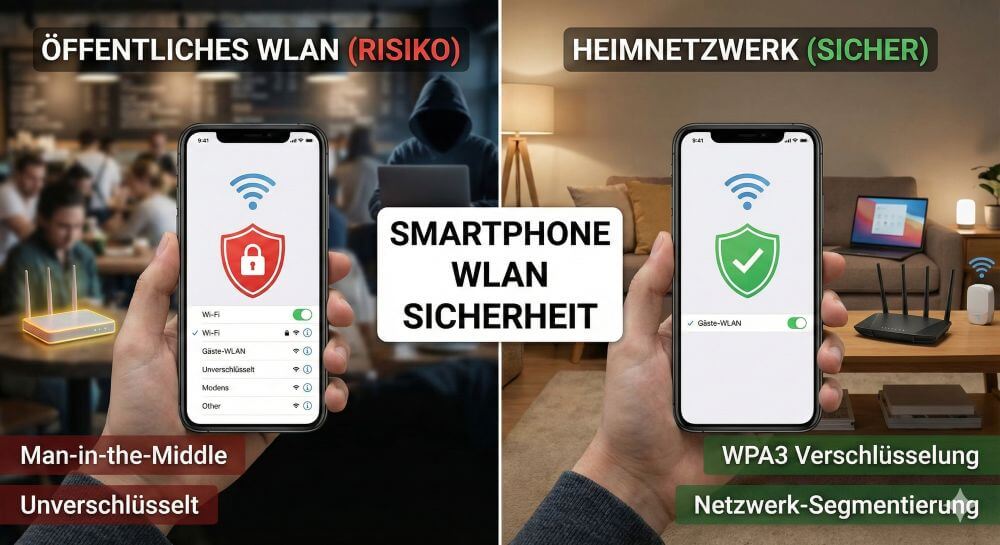
The invisible dangers: Where the risk lurks
Technical Standards: WPA2 vs. WPA3
Risk management on the go: Public hotspots
Home network: Should Wi-Fi be switched off or used permanently?
Side note: How does network segmentation work?
Conclusion
Beliebte Beiträge
From assistant to agent: Microsoft’s Copilot
Copilot is growing up: Microsoft's AI is no longer an assistant, but a proactive agent. With "Vision," it sees your Windows desktop; in M365, it analyzes data as a "Researcher"; and in GitHub, it autonomously corrects code. The biggest update yet.
Never do the same thing again: How to record a macro in Excel
Tired of repetitive tasks in Excel? Learn how to create your first personal "magic button" with the macro recorder. Automate formatting and save hours – no programming required! Click here for easy instructions.
IMAP vs. Local Folders: The secret to your Outlook structure and why it matters
Do you know the difference between IMAP and local folders in Outlook? Incorrect use can lead to data loss! We'll explain simply what belongs where, how to clean up your mailbox, and how to archive emails securely and for the long term.
Der ultimative Effizienz-Boost: Wie Excel, Word und Outlook für Sie zusammenarbeiten
Schluss mit manuellem Kopieren! Lernen Sie, wie Sie Excel-Listen, Word-Vorlagen & Outlook verbinden, um personalisierte Serien-E-Mails automatisch zu versenden. Sparen Sie Zeit, vermeiden Sie Fehler und steigern Sie Ihre Effizienz. Hier geht's zur einfachen Anleitung!
Microsoft 365 Copilot in practice: Your guide to the new everyday work routine
What can Microsoft 365 Copilot really do? 🤖 We'll show you in a practical way how the AI assistant revolutionizes your daily work in Word, Excel & Teams. From a blank page to a finished presentation in minutes! The ultimate practical guide for the new workday. #Copilot #Microsoft365 #AI
Integrate and use ChatGPT in Excel – is that possible?
ChatGPT is more than just a simple chatbot. Learn how it can revolutionize how you work with Excel by translating formulas, creating VBA macros, and even promising future integration with Office.