Google Maps gets incognito mode for more privacy
Although Google is known as well as other tech giants that they collect a huge amount of user data, which of course also explains the great success, but on the other hand, Google makes its users quite extensively possible to view the type of data collection, and also (at least in part) to limit.
Google Maps has also been re-evaluated for privacy, and will soon offer an incognito mode.
Google Maps gets incognito mode for more privacy
Although Google is known as well as other tech giants that they collect a huge amount of user data, which of course also explains the great success, but on the other hand, Google makes its users quite extensively possible to view the type of data collection, and also (at least in part) to limit.
Google Maps has also been re-evaluated for privacy, and will soon offer an incognito mode.
Storage of searched places on Google Maps can be deactivated
After Google introduced an incognito mode for YouTube at the beginning of 2019, it is now up to the Google Maps mapping service to adapt the requirements of users to data protection and to align it here.
The incognito mode can be activated by the user in the settings menu of Google Maps. As a result, information such as searched and visited places is no longer stored and used for personalized advertising and search results. According to Google, the update comes first for Android, and will soon follow for iOS.
Also, the privacy settings for the language assistant Google Assistant should be easier, said Google. In the future, saved voice commands that were last given can be conveniently deleted. All you have to do is just say: “Ok Google, delete what I said last to you”.
Although the feature with the language assistant comes in English, it should also be available in other languages in the coming months. Also, there is a new feature for the password manager, where on the one hand checks whether the password of the user in the past has ever been used for another Google Account, and also how strong the password is.
Incidentally, you can access the password manager at https://passwords.google.com/ where you can manage all passwords stored on Android and Google Chrome.
Even if you criticize the amount of data that tech companies such as Google collect, it’s exactly this data that makes the Google services we use every day possible in this quality.
The topic of data protection is becoming more and more important to us all, because more and more data is hovering around us everywhere. Therefore, it is also commendable that those who collect this data take responsibility, and provide us with the appropriate tools to (at least partially) to keep control of it.
Storage of searched places on Google Maps can be deactivated
After Google introduced an incognito mode for YouTube at the beginning of 2019, it is now up to the Google Maps mapping service to adapt the requirements of users to data protection and to align it here.
The incognito mode can be activated by the user in the settings menu of Google Maps. As a result, information such as searched and visited places is no longer stored and used for personalized advertising and search results. According to Google, the update comes first for Android, and will soon follow for iOS.
Also, the privacy settings for the language assistant Google Assistant should be easier, said Google. In the future, saved voice commands that were last given can be conveniently deleted. All you have to do is just say: “Ok Google, delete what I said last to you”.
Although the feature with the language assistant comes in English, it should also be available in other languages in the coming months. Also, there is a new feature for the password manager, where on the one hand checks whether the password of the user in the past has ever been used for another Google Account, and also how strong the password is.
Incidentally, you can access the password manager at https://passwords.google.com/ where you can manage all passwords stored on Android and Google Chrome.
Even if you criticize the amount of data that tech companies such as Google collect, it’s exactly this data that makes the Google services we use every day possible in this quality.
The topic of data protection is becoming more and more important to us all, because more and more data is hovering around us everywhere. Therefore, it is also commendable that those who collect this data take responsibility, and provide us with the appropriate tools to (at least partially) to keep control of it.
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
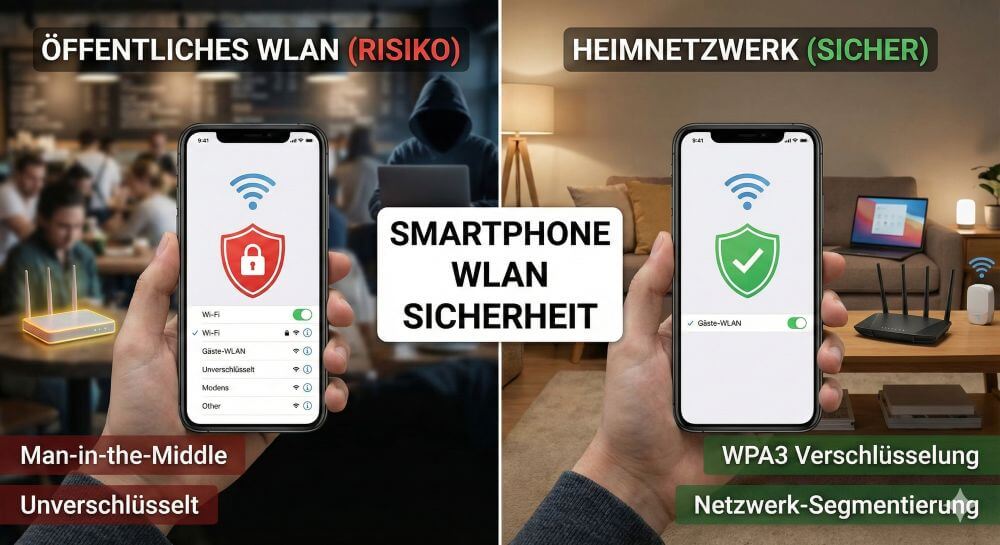
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.