Latest articles
When your own voice becomes a weapon: The rise of AI-powered audio fraud
Artificial intelligence is making the classic grandparent scam more dangerous than ever. Criminals need only a few seconds of audio material from social media to perfectly clone voices. This article examines the technology behind "deepfake calls," presents real-life case studies, and explains effective protective measures such as the family safeword.
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
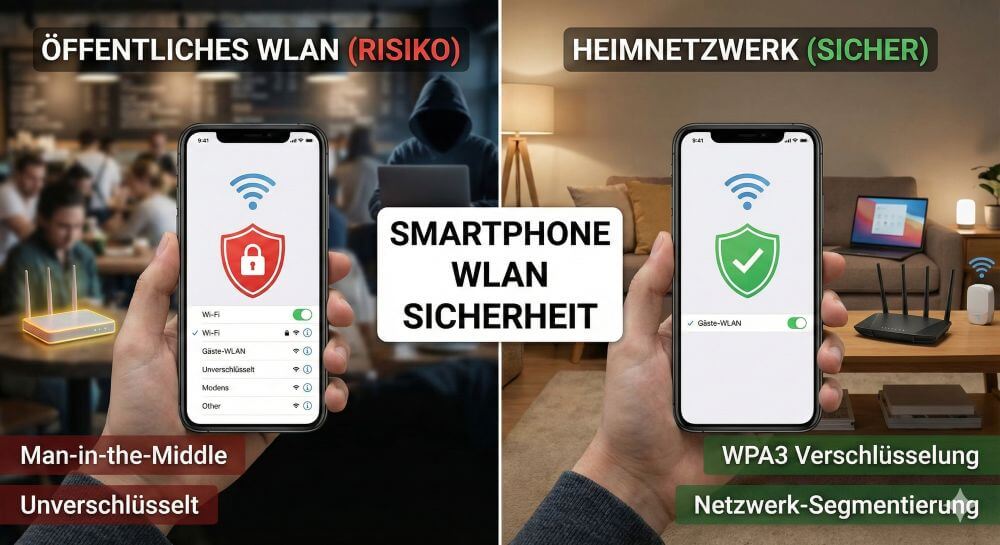
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
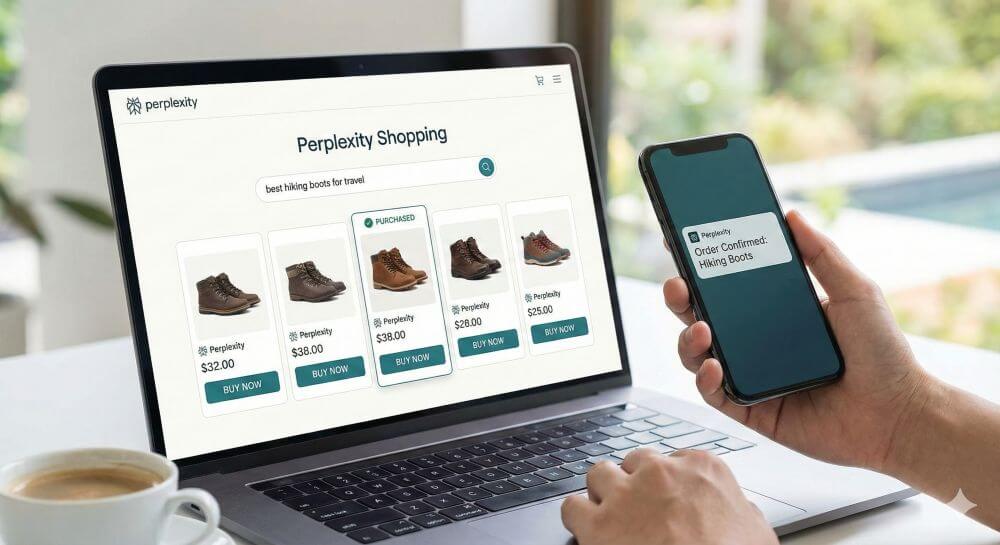
Google’s nightmare: Perplexity becomes a shopping machine
Traditional online shops are a thing of the past. With its PayPal integration, Perplexity is transforming AI search into a sales machine. Why direct purchasing via chat ("Buy with Pro") is now putting massive pressure on Google and Amazon.
Daily AI news
Werden Sie Gastautor auf unseren Seiten
As a guest author on our site, you’ll receive valuable benefits. Your articles will be reviewed and optimized by a dedicated team of editors to ensure your message comes across clearly and powerfully. You’ll become part of a growing community of writers and readers eager to read and share your words. Furthermore, you can build your authority in your field and strengthen your online presence through a dofollow backlink.
Training Data Liability: Tech-Aktien im freien Fall
Der KI-Boom steht auf wackeligen Füßen. "Training Data Liability" (Haftung für Trainingsdaten) wird zum Top-Risiko. Urheberrechtsklagen & DSGVO-Strafen bedrohen die Geschäftsmodelle der Tech-Giganten. Warum der Markt jetzt panisch reagiert.
Data Queries in Excel – Works with Power Query
So erstellen Sie aktive Datenabfragen durch Power Query aus verschiedensten Quellen in Excel, führen Daten aus verschiedenen Dateien und Tabellen zusammen.
Account hacked: Here are the actions you should take
Hack your account? Act fast! Our guide shows how to secure your account, limit damage and avoid future hacks. It is important to proceed in a structured manner.
Who owns Google? – Which companies belong to Google?
Who actually owns Google is a frequently asked question that we want to break down here, as well as which companies belong to Google.
Russia now has its own Internet
The information that will be found online in Russia in the future will be heavily regulated by a new law. Critics fear political censorship behind it.