Transparenz: Um diesen Blog kostenlos anbieten zu können, nutzen wir Affiliate-Links. Klickst du darauf und kaufst etwas, bekommen wir eine kleine Vergütung. Der Preis bleibt für dich gleich. Win-Win!
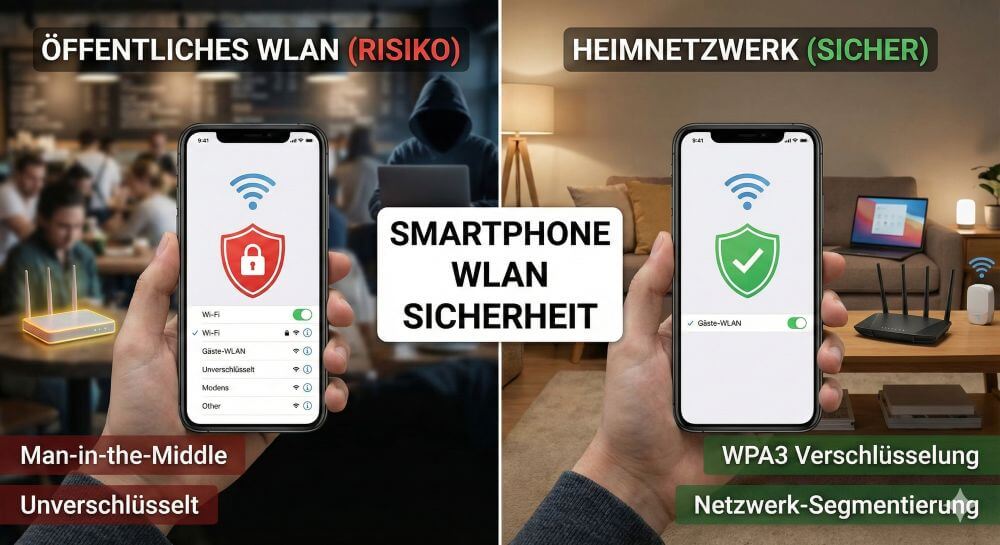
Smartphone Wi-Fi security: Public hotspots vs. home network
The smartphone has become the central hub of our digital lives. We use it for confidential banking transactions, private communication, and accessing company data. Wireless connectivity via Wi-Fi is by far the most convenient, but often also the most vulnerable interface. While we usually feel safe at home, public hotspots often resemble a digital minefield.
In this article, we analyze the technical threats in detail, explain the evolution of encryption standards, and provide a well-founded assessment of smartphone use within the home network.
Topic Overview
- Historic SoftBank deal & starting signal for EU regulation: The AI news on New Year’s Eve 31. December 2025
- When your own voice becomes a weapon: The rise of AI-powered audio fraud 26. December 2025
- December 26, 2025: Record workload during the holidays & final sprint in the mega-deal 26. December 2025
- Ad-free home network: Install Pi-hole on Windows 23. December 2025
- December 23, 2025: $900 billion valuation in sight & Google’s Flash launch 23. December 2025
The invisible dangers: Where the risk lurks
Wi-Fi signals don’t stop at walls; they spread spherically and are receivable by anyone within range. Without robust security measures, data traffic is as public as a postcard. There are three primary attack scenarios that users should be aware of:
The Man-in-the-Middle (MitM) Attack
In this classic attack, an attacker virtually positions themselves between your smartphone and the internet access point (the router). Imagine handing a letter to a mail carrier who opens it, copies it, or even alters the contents before resealing and delivering it to the recipient. Technically, the attacker redirects the data traffic through their own device. This allows them to intercept passwords or redirect you to fake websites that look deceptively real (phishing) even before your banking app detects the fraud.
The “Evil Twin” strategy
Hackers exploit the convenience of users and their devices. An attacker creates a Wi-Fi hotspot with the exact same name (SSID) as a trusted network, such as “Telekom_FON” or “Starbucks_Guest”. Because smartphones are programmed to automatically connect to known network names, your device might unknowingly connect to the attacker’s hotspot instead of the legitimate network. Once connected, all data traffic is routed through the attacker’s hotspot.
Packet Sniffing (Network Eavesdropping)
In unencrypted networks—that is, those that do not require a password for dial-in—data is sent through the air in plaintext. With freely available software, attackers can record and analyze the entire data stream in the network. Although modern websites are mostly encrypted via HTTPS, apps or older web services that do not implement this encryption properly reveal sensitive metadata, browsing habits, or in the worst case, login data.
Technical Standards: WPA2 vs. WPA3
The security of any Wi-Fi connection depends entirely on the encryption protocol used. It’s crucial to understand the difference between outdated and modern standards.
While the ancient WEP protocol can be cracked in seconds today and should no longer appear in any configuration, WPA2 (Wi-Fi Protected Access 2) remains the global standard. It uses strong AES encryption, which is generally considered secure. However, WPA2 has a vulnerability in the so-called “handshake”—the moment when the device and router agree on a password. Attacks were possible at this point in the past (keyword: KRACK).
The future therefore belongs to WPA3. This new standard closes the gaps of its predecessor with a method called SAE (Simultaneous Authentication of Equals).
The decisive advantage: Even if a user chooses a relatively weak password for their Wi-Fi, WPA3 prevents attackers from guessing this password offline through brute-force attacks. Users who can should therefore switch their router to “WPA2/WPA3 Mixed Mode” or, if all devices support it, to pure WPA3.
Risk management on the go: Public hotspots
Public Wi-Fi networks in hotels, trains, or cafes are convenient, but from a technical perspective, they are “untrusted networks.” Anyone who has to use them should establish multiple lines of defense.
The most important protection is a VPN (Virtual Private Network). A VPN establishes an encrypted tunnel through the insecure public Wi-Fi network. Even if a hacker is sitting in the same cafe and intercepting the data traffic (“sniffing”), they will only see an unreadable data stream. The endpoint of this tunnel is a secure server belonging to the VPN provider or even your own router at home.
Additionally, you should disable the automatic connection function. Smartphones constantly send out search requests (“probe requests”) to find known networks. This not only reveals where you’ve previously connected (e.g., “WiFi_Company_Mueller”, “Hotel_Paris”), but also makes the device vulnerable to the Evil Twin attacks described above. Therefore, regularly delete old Wi-Fi profiles or disable the “Auto-connect” function for public networks.
This not only reveals your previous network locations (e.g., “WiFi_Company_Mueller”, “Hotel_Paris”), but also makes the device vulnerable to the Evil Twin attacks described above. Therefore, regularly delete old Wi-Fi profiles or disable the “Auto-connect” function for public networks.
An often overlooked point is tracking. To prevent department stores or airport operators from creating movement profiles of you, modern smartphones use randomized MAC addresses. This means that the phone identifies itself to each Wi-Fi network with a new, randomly generated hardware address, instead of displaying its real, unchanging identifier. This feature should always remain enabled on Android and iOS.
Home network: Should Wi-Fi be switched off or used permanently?
A frequently discussed question among security-conscious users is whether to disable Wi-Fi on their smartphones at home to minimize potential attack surfaces.
Why a permanent connection at home is secure
Unlike public hotspots, in your home network you have full control over the environment (“Trusted Environment”). If your router is running the latest software and protected by a strong, unique password and WPA2/WPA3 encryption, the risk of an external attack is extremely low. A hacker would have to be physically near your home and then specifically attempt to break your encryption – an effort that is highly unlikely for the average user.
The Disadvantages of Disabling Wi-Fi
Disabling Wi-Fi at home is often counterproductive in practice. Many essential maintenance functions of modern smartphones rely on a stable Wi-Fi connection. Automatic backups to the cloud (e.g., iCloud or Google Photos) are usually only performed over Wi-Fi to conserve mobile data. If you turn off Wi-Fi, you risk data loss in the event of a device malfunction, as there will be no current backup. App updates and security patches for the operating system are also often delayed. Furthermore, the connection to local smart home devices (such as Sonos speakers or lighting controls) is interrupted, as these usually require direct communication on the same network.
The Professional Strategy: Network Isolation via Guest Wi-Fi
Anyone who still has concerns—for example, because a potentially malware-infected smartphone could attack other devices on the network (such as the NAS drive containing tax documents)—should consider network segmentation. Most modern routers offer a guest Wi-Fi network. This is a separate network that grants internet access but blocks access to other devices on the main network.
It’s an excellent security strategy to permanently relegate not only guests but also all “unsafe” devices (smartphones, tablets, and especially IoT devices like smart bulbs or robot vacuums) to the guest Wi-Fi network. This way, you enjoy the convenience of a Wi-Fi connection for updates and browsing while simultaneously protecting your sensitive data on PCs and hard drives on the main network from potential access by compromised apps on smartphones.
Side note: How does network segmentation work?
The term “network segmentation” sounds complicated, but the principle behind it is simple. Imagine your home network as a house.
The scenario without segmentation (The “open house”)
In a typical home network, all devices are in the same “room.” Your laptop, smartphone, smart refrigerator, and security camera are all located in the living room.
- The problem: If an intruder (hacker or virus) climbs in through an unsecured window (e.g., a cheap smart bulb or an infected app on your phone), they are standing right in the middle of the room. They can immediately go to the desk where your PC with your banking information is located, or to the cabinet with your private photos (NAS drive). There are no obstacles.
The scenario with segmentation (The “Guesthouse principle”)
With network segmentation, your router builds a solid wall. He divides the network into two (or more) separate areas:
- The main network (The vault): This is where only your trusted, critical devices (PC, laptop, data storage/NAS) are located.
- The guest network (The conservatory): This is where devices that need internet access but don’t need to access your sensitive data are located (smart lights, robot vacuums, the PlayStation, and, of course, your smartphone).
How does this work technically?
- The router acts as a gatekeeper.
- Towards the Internet: The router allows both rooms (main network and guest network) to access the internet. So you can easily browse, stream, and chat on the guest Wi-Fi.
- Towards the In: The router rigorously blocks any attempt by a device from the “conservatory” (guest Wi-Fi) to open the door to the “vault” (main network).
Why is this brilliant for smartphone users?
If you use your smartphone on the guest Wi-Fi network and accidentally pick up malware, the virus is trapped in the “conservatory” (the network’s external network). It can try to spread within the network, but it bounces off the wall connecting it to the main network. Your PC with the tax documents on the other network segment remains invisible and untouchable for the attacker.
Conclusion
Wi-Fi security requires a nuanced approach. In public spaces, the principle of “Zero Trust” applies: distrust any open network and consistently use VPN services and tracking protection.
At home, however, the benefits of a stable Wi-Fi connection far outweigh the theoretical risk. As long as the router is properly configured, you can and should leave Wi-Fi enabled on your smartphone to ensure updates and backups. Those who want to maximize security can use segmentation via a guest network instead of sacrificing convenience.
Search for:
You might also be interested in:
Latest Posts:
- Historic SoftBank deal & starting signal for EU regulation: The AI news on New Year’s Eve
- When your own voice becomes a weapon: The rise of AI-powered audio fraud
- December 26, 2025: Record workload during the holidays & final sprint in the mega-deal
- Ad-free home network: Install Pi-hole on Windows
- December 23, 2025: $900 billion valuation in sight & Google’s Flash launch
- How to tune your FRITZ!Box into a professional call server
About the Author:
Beliebte Beiträge
Header and footer in Word – First page different in Word
Michael2023-06-04T09:01:51+02:00March 29th, 2023|Categories: Shorts & Tutorials, Microsoft Office, Microsoft Word, Uncategorized|Tags: letters, Word|
How to make headers different on the first page than on the rest of the pages. Also create custom footers in Word for your documents.
Clean up Excel spreadsheets
Michael2023-06-04T09:05:39+02:00March 27th, 2023|Categories: Shorts & Tutorials, Microsoft Excel, Microsoft Office, Uncategorized|Tags: Excel, Excel tables|
It is very easy to use Excel tables created without a system and still get usable data from them with a few tricks.
Insert and edit header and footer in Excel
Michael2023-06-03T16:46:56+02:00February 5th, 2023|Categories: Shorts & Tutorials, Microsoft Excel, Microsoft Office, Office 365|Tags: Excel, Excel Calendar, Excel tables|
Inserting a header and footer in Excel is far from user-friendly. We show ways and workarounds how you can do it anyway.
Concatenate text and date in Excel – Tutorial
Michael2023-06-03T16:47:55+02:00November 16th, 2022|Categories: Microsoft Excel, Microsoft Office, Office 365, Shorts & Tutorials|Tags: Excel, Excel tables|
Concatenating text and date in Excel requires a combination of two functions. We use a practical example to explain how it can be used.
Create and save your own text modules in Word
Michael2023-06-03T16:48:50+02:00October 22nd, 2022|Categories: Microsoft Office, Microsoft Word, Office 365, Shorts & Tutorials|Tags: letters, Word|
Create your own text blocks in Word, save them and quickly add ready-made text and graphics to your documents.
Data Queries in Excel – Works with Power Query
Michael2023-06-03T16:49:44+02:00September 27th, 2022|Categories: Microsoft Excel, Microsoft Office, Office 365, Shorts & Tutorials|Tags: Excel, Excel tables|
So erstellen Sie aktive Datenabfragen durch Power Query aus verschiedensten Quellen in Excel, führen Daten aus verschiedenen Dateien und Tabellen zusammen.