The most important tips for online banking
The number of participants in online banking is growing, and is enjoying increasing enthusiasm.
In the year 2018, 50% of Germans now have online access to their checking account. Nevertheless, on closer examination, the proportion has grown by only about 5% in the past 5 years. The reasons for this are among others, often the recurrent reports about security vulnerabilities, or stolen records. Of course, this does not necessarily create trust among customers.
In part, however, it is also the case that the users even by ignorance, or negligence, your data in the hands of scammers, or at least make it easy. In our article, we would like to point out the most important points from our point of view, so that you can do your money conveniently and, above all, safely from home.
The most important tips for online banking
The number of participants in online banking is growing, and is enjoying increasing enthusiasm.
In the year 2018, 50% of Germans now have online access to their checking account. Nevertheless, on closer examination, the proportion has grown by only about 5% in the past 5 years. The reasons for this are among others, often the recurrent reports about security vulnerabilities, or stolen records. Of course, this does not necessarily create trust among customers.
In part, however, it is also the case that the users even by ignorance, or negligence, your data in the hands of scammers, or at least make it easy. In our article, we would like to point out the most important points from our point of view, so that you can do your money conveniently and, above all, safely from home.
1. Overview of the TAN procedure
1. Overview of the TAN procedure
After many attempts by the banks, the following procedures have now been established:
Although there are other methods, but basically it is as you have already noticed, always about as safe as possible to create a TAN or transfer.
After many attempts by the banks, the following procedures have now been established:
Although there are other methods, but basically it is as you have already noticed, always about as safe as possible to create a TAN or transfer.
2. Browser security in online banking
2. Browser security in online banking
Regardless of which of the above methods you use, they all presuppose that the entire chain of the components involved is protected.
And that includes the security of the PC and the browser used.
Note:
A good alternative to the standard browsers especially for online banking, but also for transactions via PayPal and other financial service providers offers the premium anti-virus software Bitdefender
This browser is specially secured by the attached anti-virus software to a high degree, and is absolutely recommendable from personal experience.
Regardless of which of the above methods you use, they all presuppose that the entire chain of the components involved is protected.
And that includes the security of the PC and the browser used.
Note:
A good alternative to the standard browsers especially for online banking, but also for transactions via PayPal and other financial service providers offers the premium anti-virus software Bitdefender
This browser is specially secured by the attached anti-virus software to a high degree, and is absolutely recommendable from personal experience.
3. Password security for online banking
3. Password security for online banking
Of course, all technical safety measures are useless if it fails the easiest. Namely the secure password.
Here we recommend that you think up a whole sentence that you may associate with personal events. And you should then change this as far as the e.g. every 2nd letter is capitalized, or the letter E is replaced by a 3.
You could then use special characters such as / or% between the words.
Basically, the more complex a password is, the better.
If you do not want to think of anything, you can also create an Online Password Generator. But it is better that you think your own.
Of course, all technical safety measures are useless if it fails the easiest. Namely the secure password.
Here we recommend that you think up a whole sentence that you may associate with personal events. And you should then change this as far as the e.g. every 2nd letter is capitalized, or the letter E is replaced by a 3.
You could then use special characters such as / or% between the words.
Basically, the more complex a password is, the better.
If you do not want to think of anything, you can also create an Online Password Generator. But it is better that you think your own.
4. Protection against phishing in online banking
4. Protection against phishing in online banking
The methods that scammers are trying to get at your bank details are almost limitless.
In any case, you should pay attention to the following points to make it as difficult as possible for such people:
The methods that scammers are trying to get at your bank details are almost limitless.
In any case, you should pay attention to the following points to make it as difficult as possible for such people:
5. Free checking accounts in comparison
5. Free checking accounts in comparison
6. Installment loans in comparison
6. Installment loans in comparison
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
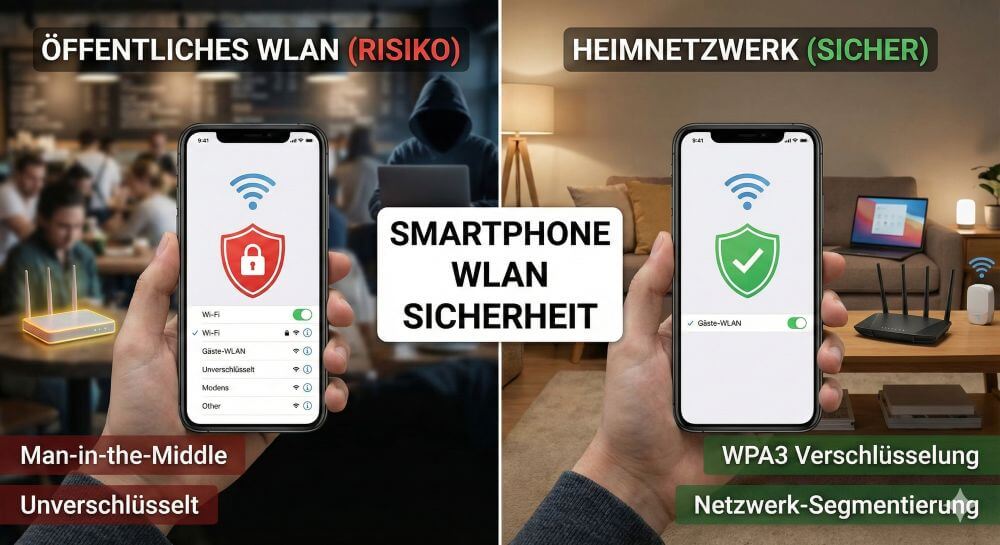
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.