When your own voice becomes a weapon: The rise of AI-powered audio fraud
For a long time, phishing emails with poor grammar were the primary tool of cybercriminals. But with the rapid advancement of generative artificial intelligence (AI), the threat potential has changed dramatically. Today, a short audio snippet is enough to clone an ordinary person’s voice with uncanny realism.
This phenomenon, known as “voice cloning” or “deepfake audio,” is revolutionizing scams like the classic “grandchild scam.”

The technology: Three seconds are enough
Where the fraudsters got your vote from
The fraud scenarios
Statistics and risk perception
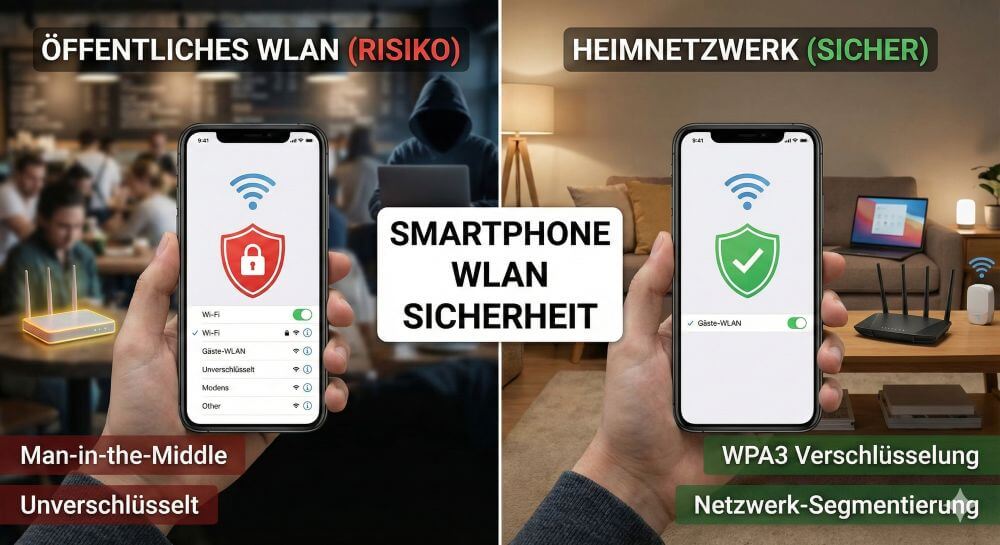
How to protect yourself
Beliebte Beiträge
Create a Word letter template with form fields
Create a professional DIN 5008 letter template with form fields and drop-down lists in Microsoft Word, and write letters as easily as you would fill out a form.
Protect Word documents from editing
Protect your documents in Microsoft Word from unauthorized editing or block access completely.
Show and remove duplicate entries in Excel | Tutorial
We explain how to remove duplicate entries from Excel. And also how you can only display duplicate entries in Excel but not delete them immediately in order to decide on a case-by-case basis.
Custom Formatting Excel – Number Format Codes Excel
We use a practical example to explain the importance and possible uses of custom formatting in Excel. Number format codes in Excel are not rocket science!
How to create a dynamic table in Excel
This is how you conveniently create a dynamic table in Excel and have it automatically carry out calculations.
Use macros correctly in Excel
Almost everyone has heard of the term "macro" in the context of Excel, and perhaps has shied away from it because it sounds like a rather complicated affair for which you have to deal with Excel programming.