How to comply with anti-virus programs state of the art for GDPR
Article 32 of the General Data Protection Regulation (DSGVO) states that companies must protect their data in accordance with the “state of the art”. Anti-virus programs can also help. The term “state of the art” already plays a role in § 8a of the Act to Increase the Security of Information Technology Systems (IT Security Act) from 2015. It is formulated here that critical infrastructures (CRITICAL) must be secured accordingly. One step further goes to Art. 32 of the GDPR. Here, the state of the art is the benchmark for IT security, when it comes to protection of personal data goes .
Even IT experts are not always in complete agreement on how to interpret this formula. What is clear, however, is that there are always security holes in German companies and the associated loss of data. These can be punished with immense punishments since May 2018.
How to comply with anti-virus programs state of the art for GDPR
Article 32 of the General Data Protection Regulation (DSGVO) states that companies must protect their data in accordance with the “state of the art”. Anti-virus programs can also help. The term “state of the art” already plays a role in § 8a of the Act to Increase the Security of Information Technology Systems (IT Security Act) from 2015. It is formulated here that critical infrastructures (CRITICAL) must be secured accordingly. One step further goes to Art. 32 of the GDPR. Here, the state of the art is the benchmark for IT security, when it comes to protection of personal data goes .
Even IT experts are not always in complete agreement on how to interpret this formula. What is clear, however, is that there are always security holes in German companies and the associated loss of data. These can be punished with immense punishments since May 2018.
1. That means state of the art
1. That means state of the art
If you want to get to the bottom of the GDPR formula “state of the art”, take a close look at the general architecture of security solutions. The first IT laws contained the term “antivirus”, the corresponding software had to be installed on all endpoints.
Affected companies had no problems making this clear move. But clear spelling out in the field of IT security is not always an advantage. This is how appropriate security solutions are also disclosed to potential cyber criminals, who usually do not find it particularly difficult to find entry points despite antivirus protection.
The first antivirus programs, based on pattern-based updates were quickly outwitted by hackers. Conversely, this means that reliability and security of IT protection depend not only on the technology itself, but also on the degree of distribution.
The last 30 years have shown that every two to three years a new technology has reached the market for endpoint security. This always had a greater impact than all of its predecessors. So if the legislature had to rewrite the IT security laws about every three years, it would make precise technologies a must.
If you want to get to the bottom of the GDPR formula “state of the art”, take a close look at the general architecture of security solutions. The first IT laws contained the term “antivirus”, the corresponding software had to be installed on all endpoints.
Affected companies had no problems making this clear move. But clear spelling out in the field of IT security is not always an advantage. This is how appropriate security solutions are also disclosed to potential cyber criminals, who usually do not find it particularly difficult to find entry points despite antivirus protection.
The first antivirus programs, based on pattern-based updates were quickly outwitted by hackers. Conversely, this means that reliability and security of IT protection depend not only on the technology itself, but also on the degree of distribution.
The last 30 years have shown that every two to three years a new technology has reached the market for endpoint security. This always had a greater impact than all of its predecessors. So if the legislature had to rewrite the IT security laws about every three years, it would make precise technologies a must.
2. Every company has its own state of the art
2. Every company has its own state of the art
Also, you can not make a general statement about what helps a business or not. Every group, every institution or company has its own risk and requirement profile with regard to IT security. Security technologies that effectively protect a large-scale enterprise can already fail the budget for a medium-sized enterprise.
An exactly prescribed security architecture may be too complex for one company, while it may not even be sufficient for the big corporation. Therefore, it makes sense that the term “state of the art” has been used in the formulation of the GDPR.
Existentially important is also the reflection that you deal with the topic of security continuously. It would be fatal to simply buy the first product.
The different interpretation of the “state of the art” raises the awareness that the security of your IT technology is not a status quo that you simply obtain in this way and that is then no longer subject to change. On the contrary: IT protection is a constant process, for which a meaningful strategy is required to always effectively protect your sensitive data.
Also, you can not make a general statement about what helps a business or not. Every group, every institution or company has its own risk and requirement profile with regard to IT security. Security technologies that effectively protect a large-scale enterprise can already fail the budget for a medium-sized enterprise.
An exactly prescribed security architecture may be too complex for one company, while it may not even be sufficient for the big corporation. Therefore, it makes sense that the term “state of the art” has been used in the formulation of the GDPR.
Existentially important is also the reflection that you deal with the topic of security continuously. It would be fatal to simply buy the first product.
The different interpretation of the “state of the art” raises the awareness that the security of your IT technology is not a status quo that you simply obtain in this way and that is then no longer subject to change. On the contrary: IT protection is a constant process, for which a meaningful strategy is required to always effectively protect your sensitive data.
3. Achieve state of the art
3. Achieve state of the art
With the anti-virus software from the extensive range of Licensing, you can achieve the state of the art that is optimal for you. After all, Lizenzking is Germany’s first address for software licenses. Business customers as well as private users get inexpensive programs for immediate download on Licenseking.de and receive a first class service. Licensing does not only offer helpful software from the areas of security & tuning, office & tax as well as multimedia & graphics, but also a large selection of Microsoft licenses.
For example, with “Kaspersky Small Office Security”. This security program is ideal for small businesses that have between five and 25 computers, mobile devices and some servers. “Kaspersky Small Office Security” is managed on a cloud-based console, which is very user-friendly.
You do not need any previous IT knowledge for this software, an out-of-the-box solution.
You can use the powerful security tools efficiently right from the start and keep an eye on the security of your connected devices. Protect your computers, file servers and other devices with „Kaspersky Small Office Security“ from a single console in order to achieve your individual state of the art.
With the anti-virus software from the extensive range of Licensing, you can achieve the state of the art that is optimal for you. After all, Lizenzking is Germany’s first address for software licenses. Business customers as well as private users get inexpensive programs for immediate download on Licenseking.de and receive a first class service. Licensing does not only offer helpful software from the areas of security & tuning, office & tax as well as multimedia & graphics, but also a large selection of Microsoft licenses.
For example, with “Kaspersky Small Office Security”. This security program is ideal for small businesses that have between five and 25 computers, mobile devices and some servers. “Kaspersky Small Office Security” is managed on a cloud-based console, which is very user-friendly.
You do not need any previous IT knowledge for this software, an out-of-the-box solution.
You can use the powerful security tools efficiently right from the start and keep an eye on the security of your connected devices. Protect your computers, file servers and other devices with „Kaspersky Small Office Security“ from a single console in order to achieve your individual state of the art.
About the Author:
About the Author:
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
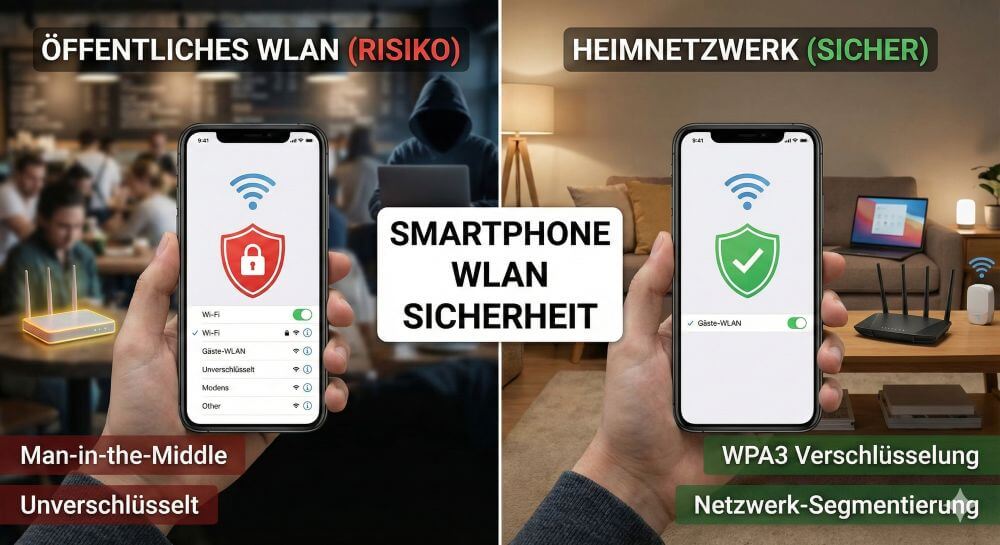
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.
Popular Posts:
Ad-free home network: Install Pi-hole on Windows
Say goodbye to ads on smart TVs and in apps: Pi-hole software turns your Windows laptop into a network filter. This article explains step-by-step how to install it via Docker and configure the necessary DNS settings in your FRITZ!Box.
How to tune your FRITZ!Box into a professional call server
A professional telephone system can be built using a FRITZ!Box and a laptop. This article shows step by step how to use the free software "Phoner" to schedule announcements and record calls – including important legal information (§ 201 StGB).
Why to-do lists are a waste of time
Do you feel unproductive at the end of the day, even though you've worked hard? Your to-do list is to blame. It tempts you to focus on easy tasks and ignores your limited time. This article explains why lists are "self-deception" and why professionals use a calendar instead.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Cybersicherheit: Die 3 größten Fehler, die 90% aller Mitarbeiter machen
Hacker brauchen keine Codes, sie brauchen nur einen unaufmerksamen Mitarbeiter. Von Passwort-Recycling bis zum gefährlichen Klick: Wir zeigen die drei häufigsten Fehler im Büroalltag und geben praktische Tipps, wie Sie zur menschlichen Firewall werden.