Useful tips about your Data Protection
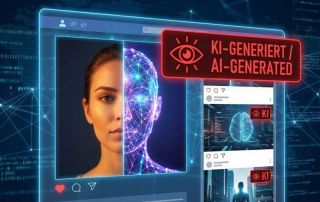
When your own voice becomes a weapon: The rise of AI-powered audio fraud
Artificial intelligence is making the classic grandparent scam more dangerous than ever. Criminals need only a few seconds of audio material from social media to perfectly clone voices. This article examines the technology behind "deepfake calls," presents real-life case studies, and explains effective protective measures such as the family safeword.