Smartphone Wi-Fi security: Public hotspots vs. home network
The smartphone has become the central hub of our digital lives. We use it for confidential banking transactions, private communication, and accessing company data. Wireless connectivity via Wi-Fi is by far the most convenient, but often also the most vulnerable interface. While we usually feel safe at home, public hotspots often resemble a digital minefield.
In this article, we analyze the technical threats in detail, explain the evolution of encryption standards, and provide a well-founded assessment of smartphone use within the home network.
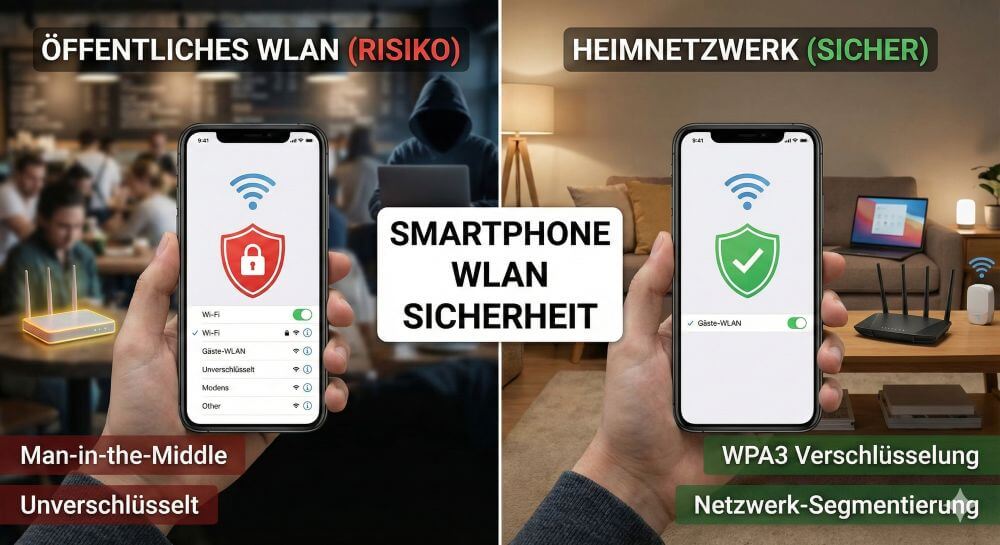
The invisible dangers: Where the risk lurks
Technical Standards: WPA2 vs. WPA3
Risk management on the go: Public hotspots
Home network: Should Wi-Fi be switched off or used permanently?
Side note: How does network segmentation work?
Conclusion
Beliebte Beiträge
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Microsoft Loop in Teams: The revolution of your notes?
What exactly are these Loop components in Microsoft Teams? We'll show you how these "living mini-documents" can accelerate your teamwork. From dynamic agendas to shared, real-time checklists – discover practical use cases for your everyday work.
Career booster 2026: These Microsoft Office skills will take you further!
A new year, new career opportunities! But which Office skills will really be in demand in 2026? "Skilled use" is no longer enough. We'll show you today's must-haves – like advanced Excel, using AI in the office, and relevant certifications for your resume.
Excel Tutorial: How to quickly and safely remove duplicates
Duplicate entries in your Excel lists? This distorts your data. Our tutorial shows you, using a practical example, how to clean up your data in seconds with the "Remove Duplicates" function – whether you want to delete identical rows or just values in a column.
Dynamic ranges in Excel: OFFSET function
The OFFSET function in Excel creates a flexible reference. Instead of fixing =SUM(B5:B7), the function finds the range itself, e.g., for the "last 3 months". Ideal for dynamic charts or dashboards that grow automatically.
Mastering the INDIRECT function in Excel
The INDIRECT function in Excel converts text into a real reference. Instead of manually typing =January!E10, use =INDIRECT(A2 & "!E10"), where A2 contains 'January'. This allows you to easily create dynamic summaries for multiple worksheets.