Please support our work
We created this blog to give our visitors real help on many topics related to the digital world. With over 280 articles and tutorials in German and more than 230 in English translation, we are on the right track. Our blog now has over 100,000 page views per month. What shows that the work is worth it!
You are welcome to support our blog with a small donation so that our work, which involves a lot of research and care, can remain free of charge for you. Because the capacities that we also need here on the technical side are unfortunately not in vain. We also support guest authors free of charge in expanding the reach of their own website through a backlink on Google. Feel free to visit our page for guest authors and write an article yourself, which we will publish in German and English. Unlike other blogs, articles remain free for guest authors and do not have a fixed term.
Please support our work
We created this blog to give our visitors real help on many topics related to the digital world. With over 280 articles and tutorials in German and more than 230 in English translation, we are on the right track. Our blog now has over 100,000 page views per month. What shows that the work is worth it!
You are welcome to support our blog with a small donation so that our work, which involves a lot of research and care, can remain free of charge for you. Because the capacities that we also need here on the technical side are unfortunately not in vain. We also support guest authors free of charge in expanding the reach of their own website through a backlink on Google. Feel free to visit our page for guest authors and write an article yourself, which we will publish in German and English. Unlike other blogs, articles remain free for guest authors and do not have a fixed term.
Popular Posts
When your own voice becomes a weapon: The rise of AI-powered audio fraud
Artificial intelligence is making the classic grandparent scam more dangerous than ever. Criminals need only a few seconds of audio material from social media to perfectly clone voices. This article examines the technology behind "deepfake calls," presents real-life case studies, and explains effective protective measures such as the family safeword.
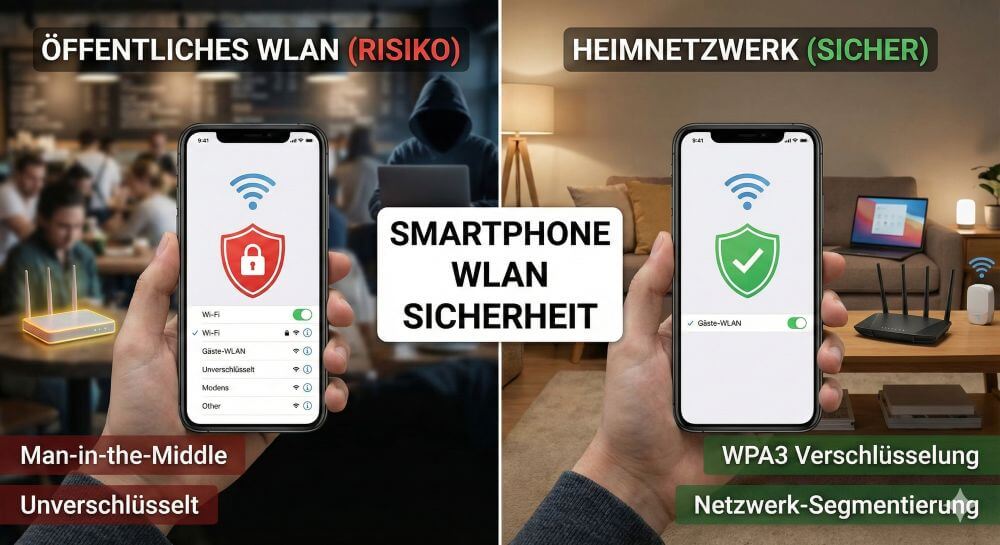
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
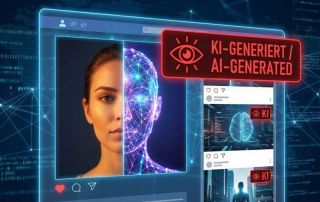
AI labeling on social media: Obligations & help with errors
No more deception: Instagram, TikTok, and YouTube are requiring users to label AI-generated content. We explain the technology, the risks for creators, and what to do if the algorithm mistakenly identifies your real photos as AI ("false positives").
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Password madness: Why passkeys are the future
The era of passwords is ending. Passkeys offer protection against phishing and make logging in as easy as glancing at your phone. But what happens when you change phones? This article explains the technology and provides important tips for securely transferring your digital keys.
Windows 10: One month after the “End of Life” – assessment and options for action
On October 14, 2025, support for Windows 10 ended. Millions of PCs are now unprotected. We examine the current security situation, the new ESU subscription model, and show solutions for older hardware – from upgrade tricks to secure Linux alternatives.
Popular Posts
When your own voice becomes a weapon: The rise of AI-powered audio fraud
Artificial intelligence is making the classic grandparent scam more dangerous than ever. Criminals need only a few seconds of audio material from social media to perfectly clone voices. This article examines the technology behind "deepfake calls," presents real-life case studies, and explains effective protective measures such as the family safeword.
Smartphone Wi-Fi security: Public hotspots vs. home network
Is smartphone Wi-Fi a security risk? This article analyzes in detail threats such as evil twin attacks and explains protective measures for when you're on the go. We also clarify why home Wi-Fi is usually secure and how you can effectively separate your smart home from sensitive data using a guest network.
AI labeling on social media: Obligations & help with errors
No more deception: Instagram, TikTok, and YouTube are requiring users to label AI-generated content. We explain the technology, the risks for creators, and what to do if the algorithm mistakenly identifies your real photos as AI ("false positives").
Warum dein Excel-Kurs Zeitverschwendung ist – was du wirklich lernen solltest!
Hand aufs Herz: Wann hast du zuletzt eine komplexe Excel-Formel ohne Googeln getippt? Eben. KI schreibt heute den Code für dich. Erfahre, warum klassische Excel-Trainings veraltet sind und welche 3 modernen Skills deinen Marktwert im Büro jetzt massiv steigern.
Password madness: Why passkeys are the future
The era of passwords is ending. Passkeys offer protection against phishing and make logging in as easy as glancing at your phone. But what happens when you change phones? This article explains the technology and provides important tips for securely transferring your digital keys.
Windows 10: One month after the “End of Life” – assessment and options for action
On October 14, 2025, support for Windows 10 ended. Millions of PCs are now unprotected. We examine the current security situation, the new ESU subscription model, and show solutions for older hardware – from upgrade tricks to secure Linux alternatives.