Trust is good, verification is everything:
Why Zero Trust doesn’t work without identity protection
In traditional IT security, a company resembled a medieval fortress. A thick wall (the “firewall”) protected a trusted internal network (“LAN”) from the “evil” outside world (“Internet”). This “castle-and-moat” model had a fatal flaw: once an attacker—or a compromised employee—had breached the wall, the entire internal network was open to them.
This model is dead.
In today’s world of cloud services, mobile devices, remote work, and globally interconnected supply chains, “inside” and “outside” no longer exist. The traditional perimeter has dissolved. The answer to this new reality is a radically different philosophy: Zero Trust. And the foundation upon which this philosophy rests is identity protection.

Part 1: The Zero Trust Philosophy – Trust no one
Zero Trust (ZT) isn’t a product you can buy. It’s a strategic security model based on a simple yet radical premise: By default, trust no one, neither inside nor outside your network.
The mantra is: “Never trust, always verify.”
Every request, every access attempt must be treated as a potential threat, regardless of its origin. A manager sitting in the office accessing the financial server is treated the same as an unknown hacker on the internet—both must prove their identity and authorization beyond any doubt each time.
The three core principles of Zero Trust are:
- Explicitly Verify: Authenticate and authorize every access based on all available data points (identity, location, device status, service, etc.).
- Principle of Least Privilege: Grant users only the minimum access they need to perform their immediate task. No more.
- Assume Breach: Assume that attackers are already in the network. Minimize potential damage through microsegmentation and continuous monitoring.
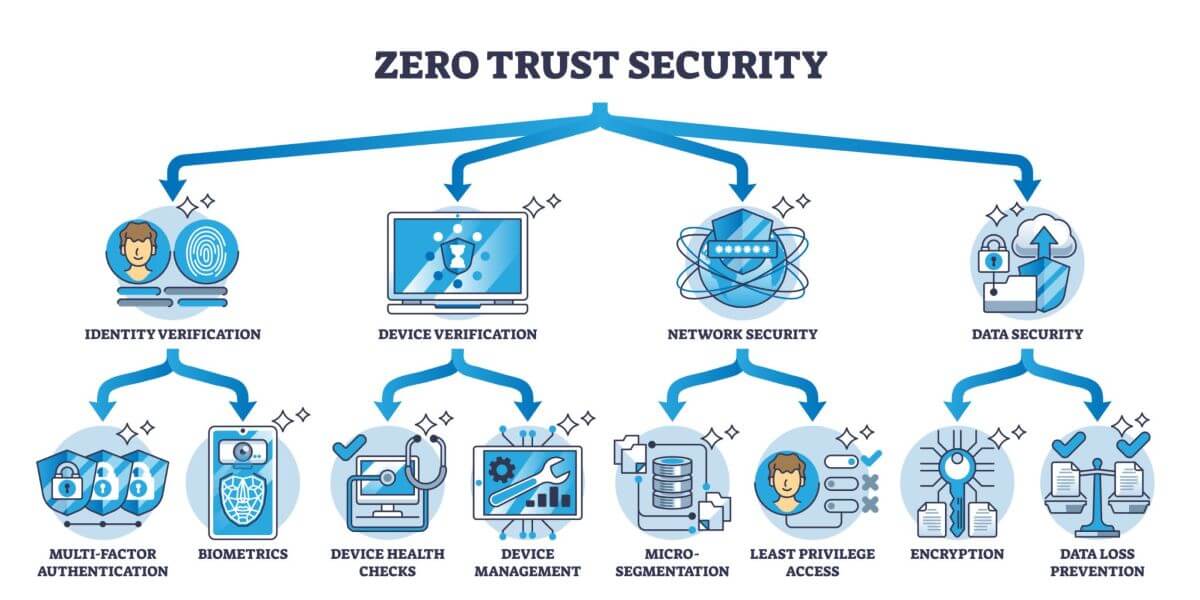
Part 2: Identity Protection – The New Perimeter
If the network is no longer the perimeter, what is? Identity is the new perimeter.
If Zero Trust is the demand (“Verify everyone!”), identity protection is the answer (“This is how we verify!”). Without robust mechanisms for managing and protecting identities, Zero Trust remains an empty promise.
Identity protection encompasses all the technologies and processes that ensure a user (or device or service) is who they claim to be and that they are only allowed to do what they are authorized to do.
Part 3: The building blocks: How identity protection implements Zero Trust
Zero Trust is achieved through the interplay of multiple identity protection technologies.
1. The Foundation: Multi-Factor Authentication (MFA)
This is the absolute, non-negotiable foundation. A single password is not enough. MFA requires a user to prove their identity through a combination of factors:
- Knowledge: Something only the user knows (e.g., a password).
- Possession: Something only the user has (e.g., a smartphone with an authenticator app or a USB security key).
- Inherence: Something the user is (e.g., a fingerprint or a facial scan).
In a Zero Trust model, MFA is enforced for every access, not just the initial login.
2. The Control Center: Identity & Access Management (IAM)
IAM systems are the brain of identity protection. They are a central database for all identities (employees, partners, customers, but also devices and applications).
- Authentication: The IAM system verifies: Is this really you? (e.g., by requesting a password + MFA token).
- Authorization: The IAM system verifies: Are you allowed to do this? (e.g., by assigning roles such as “Read,” “Write,” or “Admin”).
Here, the principle of least privilege is technically implemented.
3. The Intelligent Guardian: Context-Based Access (Conditional Access)
Here, Zero Trust and identity protection merge most visibly. Conditional Access is the dynamic enforcement of access rules in real time.
The system doesn’t just ask “Who are you?”, but “Who are you in this context?”
A modern IAM system can enforce policies like this:
- IF a user from “Accounting” (identity) AND from a known, company-owned laptop (device status) AND from Germany (location), THEN allow access to the finance app with MFA.
- BUT IF the same user (perhaps with stolen data) AND from an unknown device AND from an unusual country (e.g., North Korea), THEN block access immediately and enforce a password reset.
This context-based access is the practical implementation of the “Explicit Verification” principle.
4. The High-Security Sector: Privileged Access Management (PAM)
Attackers don’t target normal user accounts, but rather administrator accounts (privileged accounts). These “privileged” accounts are the keys to the kingdom.
PAM solutions are specialized tools for managing these super-user accounts:
- Just-in-Time (JIT) Access: An administrator doesn’t always have administrator rights. They must explicitly request them for a limited period (e.g., 30 minutes) and state the reason.
- Session Monitoring: All actions of an administrator are recorded.
- Vaulting: Passwords for critical systems (e.g., database root) are stored in a digital vault and automatically rotated.
5. The Watchdog: User and Entity Behavior Analytics (UEBA)
This is the implementation of the “Assume Breach” principle. User and Entity Behavior Analytics (UEBA) uses machine learning to learn the “normal” behavior of each user and device.
The AI detects anomalies that could indicate a compromise:
Why does an employee who always works from 9 a.m. to 5 p.m. suddenly log in at 3 a.m.?
Why does a marketing employee try to access developer servers?
Why does a user suddenly download 100 GB of data when they usually only transfer a few MB per day?
The system raises an alarm in such cases, even if the attacker is using valid login credentials.
Conclusion: An inseparable synergy
Zero Trust is just an empty shell without robust identity protection. Conversely, modern identity protection without the Zero Trust philosophy is merely a collection of tools without an overarching strategy.
- Zero Trust is the strategy: Trust no one.
- Identity protection is the tactic: Use MFA, IAM, Conditional Access, and UEBA to verify identity at every single step.
The transition to Zero Trust is not a sprint, but a continuous journey. But it is a journey that is absolutely necessary – and it begins and ends with the control and protection of digital identity.
Beliebte Beiträge
Create annual calendar 2022 in Excel
In our tutorial we describe how you can create an annual calendar for 2022 with a display of the calendar week and public holidays in Excel, and use it anew every year.
Create individual charts in Excel
Charts are created quickly in Microsoft Excel. We explain how you can customize them, and also swap (transpose) the axes.
Create professional letter templates in Word
How to create a professional letter template with form fields in Microsoft Word, and only have to fill in text fields.
Create a digital signature in Outlook and Word
Create a digital signature in Microsoft Outlook and Word for more security.
Create a Table of Contents in Word
To create a dynamic table of contents in Microsoft Word - Office 365
Use bookmarks and cross-references in Word
How to use text markers to make your Word document dynamic and click through your pages.